After writing the same scripts several times I decided it is time for a generic solution to check Debian servers for configuration consistency. As incidents and mistakes happen each organization collects a set of learnings (let's call it policies) that should be followed in the future. And one important truth is that the free automation and CM tools we use (Chef, Puppet, Ansible, cfengine, Saltstack...) allow to implement policies, but do not seem to care much about proofing correct automation.
How to ensure following policies?
But how to really ensure following these policies? The only way is by
checking them and revisiting the check results frequently. One could build a script and send a daily/weekly mail report. This is always a custom solution and that's what I did several times already. So I do it one final time, but this times in a generic way.
Generic Policy Scanning
For me a generic configuration consistency / policy scanner has at least the following requirements:
- Optional generic pre-defined policies
- Optional custom user-defined policies
- Policies checked locally on the host
- Policies checked from CM systems
- Per host/hostgroup policy enabling
- Generic discovery of your hosts
- Dynamic per policy/group/host result filtering
- Customizable mail reports
- Result archival for audits
- Some simple trending
- Daily diffs, New findings, Resolved Isses
- Acknowledging Findings
I started implementing a simple solution (entirely bash and SSH based, realizing requirements 1,2,3,4,6,7,9,10) with
https://github.com/lwindolf/polscan. It is quite easy to setup by configuring the type of
- Host list provider (e.g. Chef, Puppet, mcollective)
- SSH access available
- Sudo yes/no
and you can run it instantly with the default set of policy scanners (which of course not necessarily all make sense for all type of systems).
Implemented Scanners
By setting up the results and the static HTML (instructions in README.md) in some webserver document root you can browse through the results.
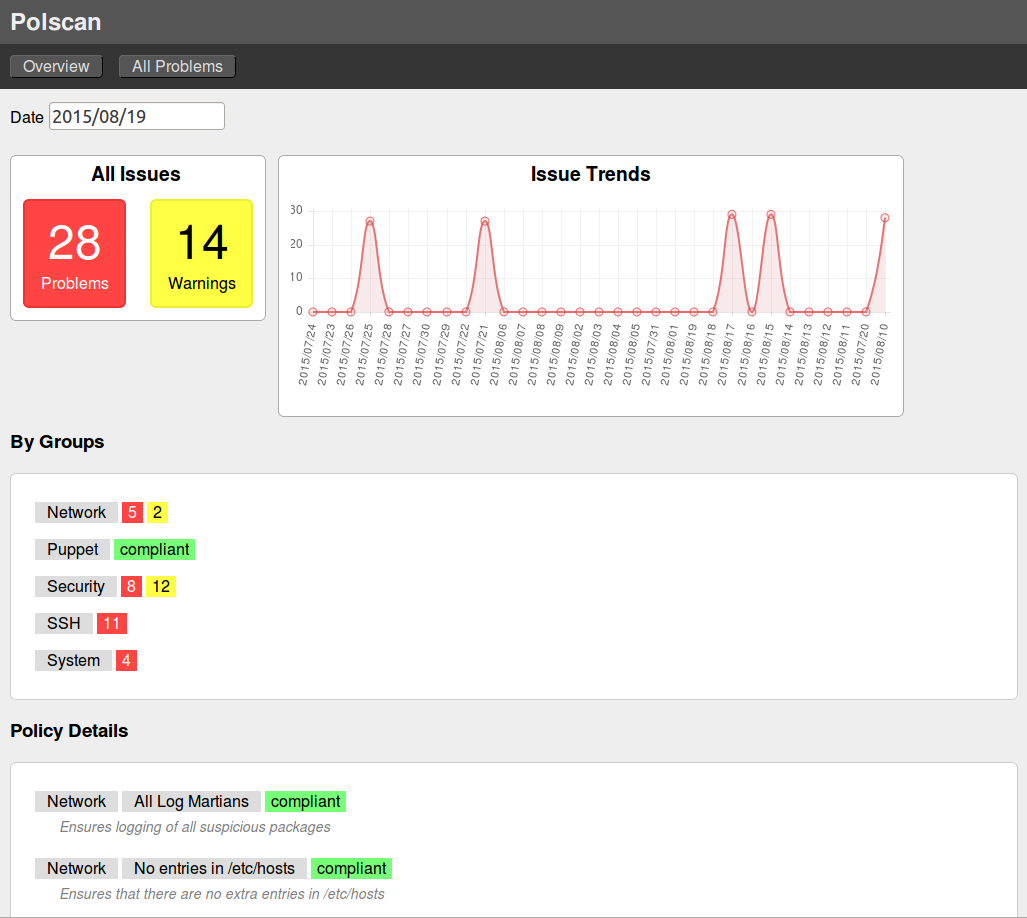
Screenshots
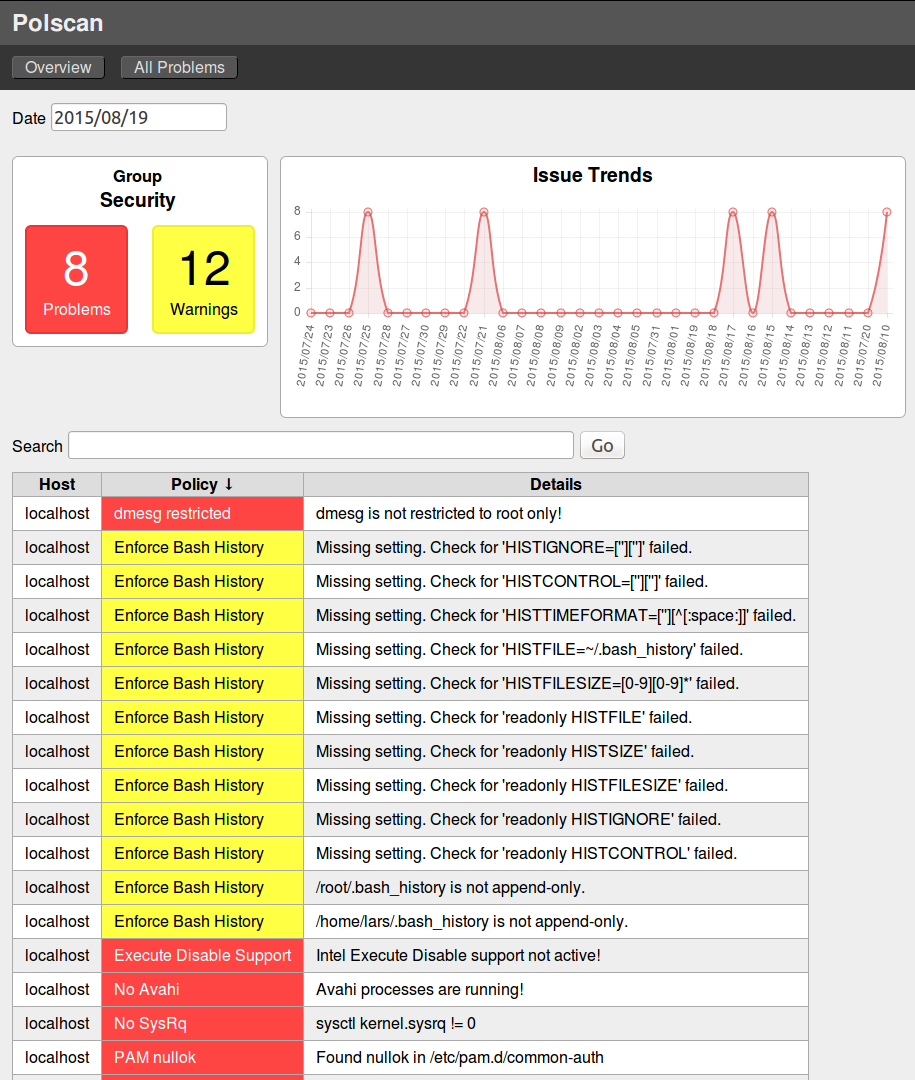
Result overview:
Filter details: